Watch list screening has been one of the pillars for know your customer (KYC) and anti-money laundering (AML) regulatory requirements since the beginning. It was introduced to prevent known criminals (or known high risk entities) from utilizing financial institutions’ networks for money laundering, and allowing financial institutions to deal with high-risk entities more appropriately. In theory, watch list screening seems to be a simple compliance requirement. But over the years, it has proved to be one of the rules with the highest false-positive rate.
Problems caused by inefficient watch list screening
The impact of an inefficient watch list screening system include:
- The risk of accepting known criminals or allowing them to utilize financial institutions’ network for money laundering or terrorist financing.
- The risk of turning down a good, genuine customer.
- Cost to investigating a large volume of watch list matches.
Watch list screening challenges
Since the rise of cryptocurrency and FinTech, financial institutions have attempted to provide services to customers in a more convenient and efficient way. This includes faster payment and easier and faster access to opening accounts. Both expose financial institutions to additional risks.
In the past, financial institutions had more time for watch list or sanction list processing. They may use a simple rule to match customers against entities in the watch list, assign investigators to investigate matches produced by the system, and then make a decision whether to accept or decline a transaction or account opening request. Now, time is an added constraint that's forcing financial institutions to revisit their current watch list screening system to see how it can perform more quickly and effectively.
As observed over the years, these are common challenges found in watch list screening:
- Missing or incomplete data: Incomplete data may come from the watch list or customer side. For example, we might want to consider date of birth as a matching criterion, but sometimes the only available data for an entity in the watch list is year of birth. This makes it difficult for financial institutions to reduce false matches by introducing a more stringent matching criteria, as it may create a risk of allowing the known criminal slipping through the screening process.
- Internationality of the data: Watch list data is international. The common problem found is the name transliteration from language using non-Latin script to the name in Latin script. The transliterate method is not standardized which causes variations in the names. For example, “Mohammed” could be written as “Muhammad,” “Muhammed,” “Mohammad,” or “Mohamad,”; or the Chinese family name “Chau” and “Chao”, though they sound similar, are two entirely different family names.
- Misspelled data: Misspelled data from data entry could cause the match to be generated unnecessarily, or worse, it could prevent a match from occurring when it should.
- Misplaced data: Sometimes data could be misplaced. For example, part of an address was provided as part of the name, or part of the name (usually name that has more than 3 tokens) was put as other information.
As a precaution, financial institutions usually take a conservative approach to the matching. In other words, they lived with additional costs for investigation, additional time taken to review the transactions or account opening requests, all just to prevent themselves from the risk of allowing potential criminals or money launderers to transact with them, which could result in regulatory fines and reputation damage. However, as the world is shifting towards faster payments and services, this might not be an acceptable anymore.
Watch list matching tuning methodology
The watch list matching process is not one-size-fit-all; the best method for each financial institution may differ. The process itself is as much an art as it is a science. It's not a pure technical problem where we can throw all possible techniques into the system and hope it will work; it's more of an understanding of the problem -- articulating, framing and dividing it into smaller problems of a manageable size -- and then finding the right technique to tackle it.
The watch list matching tuning methodology consists of five steps:
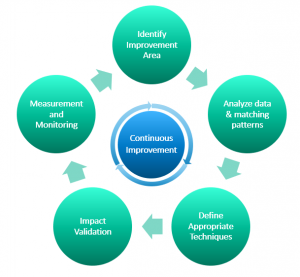
1. Identify improvement area.
A common mistake in implementing watch list screening in financial institutions is the reliance solely on expert opinion to define the matching criteria. Though it's typical to define the watch list matching criteria based on expert opinion, it should only be used as a starting point. Once we set the ball rolling with the initial matching criteria, we should take time to review the outcome of the matching produced by the initial stage of the watch list screening. Then, we could use the information to identify the improvement areas where the current matching criteria were lacking, inefficient or ineffective.
It's also important to define the objective of tuning the watch list matching. Two common objectives are: improve the matching coverage (find potential true matches not currently detected by the system) or reduce false-positives (attempt to reduce false matches while maintaining the same true matches found).
Defining the right objective is the most critical task of the tuning activity. It will set the direction for how the tuning will go and what the results will look like. Setting the objective to improve the matching coverage will unavoidably increase the number of watch list matches produced by the system, for example. It is recommended that we focus on one objective at a time. Otherwise it will be difficult to quantify changes made and impact level for changes made to meet each objective. From the high-level objective, we could also identify an objective at a finer level. For example, if we saw that the system produces a lot of (false) matches for entity customers, then we could set the objective specific to reducing those false-positives.
2. Analyze data and matching patterns.
Once the objective has been set, the next step is to analyze the data and identify matching patterns. This will help in understanding the patterns of the data, the matching and, possibly, patterns of false matches. The analysis in this case ranges from simplistic methods such as SQL-query, to more advanced methods, such as the use of data quality assessment tools and techniques or natural language processing techniques to uncover hidden patterns of the data. The outcome of this step will be to define the “subset” or “partition” of the matching to be tuned.
3. Define appropriate techniques.
This step is to define techniques to be used for fine-tuning the watch list matching process, and to actually implement the fine-tuning into the watch list screening system.
4. Impact validation
The impact validation step will apply the recently tuned watch list matching process to the population. This will be used to assess the impact of the new watch list matching process in two aspects: quantity and quality.
In terms of quantity, we should quantify the number of watch list matches produced prior- and post- changes. This will help in understanding if the volume make sense, especially if the objective is to improve the coverage, and if the new watch list matches volume (which will be higher) can be handled operationally.
But the assessment in terms of quality is usually more important than quantity. This is because the quality assessment will ensure the watch list matches that differ prior- and post- does not reduce the quality of the true match produced by the watch list screening system. Especially in case of false-positive reduction, we want to ensure that the watch list matches reduced do not include those true-positive matches.
5. Measurement, monitoring and continuous improvement.
The final step is measurement and monitoring. Once the watch list screening is in use, it's important to continuously monitor the performance of the system. Rome wasn't built in a day, and it's the same with watch list screening criteria. The focus should be on the continuous improvement rather than the perfection at day one.
In order to continuously improve the effectiveness of the system, one need to be able to assess and measure its performance. Common measurements are false-positive rates and false-negative rates. The method to obtain false-negative rates is not simple and may involve creating additional review processes to validate if there is any (potential) watch list matches slip through.
Conclusion
This watch list matching tuning methodology can help you achieve a more effective, more efficiencient and better performing watch list screening system, capable of supporting business changes. The methodology emphasizes continuous improvement of the process, as well as each step within each cycle of improvement.
Learn more about how SAS Anti-Money Laundering equips financial institutions with the watch list matching functionality, methodology, data management, data quality and analytical tools required to undertake this important task.
